Scope – Gaining the Azure Data Engineer Associate Certification
The next concept that is important to RBAC is scope. Notice the hierarchical structure illustrated in Figure 1.25.
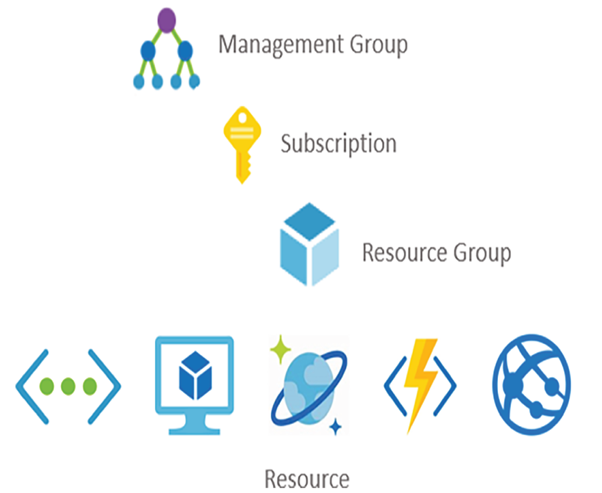
FIGURE 1.25 Role‐based access control scope
A management group is the top level, and it can be used to define different departments within a company—for example, IT, Finance, HR, and Accounting. Each of those may be responsible for managing their own spending and therefore would want to have control over all the subscriptions for which they receive the bill. A subscription is the second level and is the bill unit; it is the place where Azure resources are provisioned into. When you provision any Azure product or feature, you must provide the associated subscription. You might imagine that a company would have numerous ongoing projects that require a set of different products and features. If you were to put them all directly into the subscription bucket, it would be hard to visually group each product into their respective projects. This is where resource groups come in. You can name a resource group based on a project and then place those resources into that group. It is an organizational unit that helps structure and categorize your Azure resources. Keep in mind that a resource can only be assigned to a single resource group.
So, what does all that have to do with scope? Well, when you place an individual into a group and then grant that group a role, the next step is to give that group access to Azure resources. You can do that at any level, as shown in Figure 1.25. Two locations are likely inefficient, such as at the top management group and at the bottom to a specific resource. Granting access at the top would give the group access to all Azure resources in all Azure subscriptions. Granting access at the resource level gives access to a specific resource and all members are constrained to only that resource. The other two, subscription or resource group, make the most sense. It depends on the role and the expectations the Azure administrator has of that role. Granting access at the subscription level gives the group access to all the included resource groups and all resources within them. Granting access to the resource group gives permissions on all the resources only within the resource group.
Attribute‐Based Access Control
Attribute‐based access control (ABAC) is in PREVIEW (or beta) as of this writing. ABAC builds on RBAC and uses an additional check based on attributes. For example, say you have provisioned an ADLS Gen2 and have loaded up thousands of files. Some of those files are highly confidential, whereas others are public. If you grant a group read access on that ADLS container, it means they can read all the files, regardless of sensitivity level. Instead, you can set an attribute on each file and add an ABAC condition to the permission based on that sensitivity attribute.
The next concept that is important to RBAC is scope. Notice the hierarchical structure illustrated in Figure 1.25. FIGURE 1.25 Role‐based access control scope A management group is the top level, and it can be used to define different departments within a company—for example, IT, Finance, HR, and Accounting. Each of those may be responsible…

Archives
- August 2024
- July 2024
- June 2024
- May 2024
- April 2024
- March 2024
- February 2024
- January 2024
- December 2023
- November 2023
- October 2023
- September 2023
- July 2023
- May 2023
- April 2023
- March 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- September 2022
- May 2022
- April 2022
- February 2022
- January 2022
- December 2021
- October 2021
- September 2021
- August 2021
- June 2021
- May 2021
- April 2021
Contact US